
CAVEAT: The information provided herein is most likely exactly correct, HOWEVER use it at your own risk: we assume no risk or liability. Do your own evaluation and make your own choices.
In previous articles we have revealed our approach to identifying what resources are needed in the public training computer lab, how to select, purchase, and assemble components to build the needed computer hardware, and how to install the operating system(s) onto that hardware so that it can be used.
In this article we review additional programs which should be installed, needed configuration steps to make that hardware maintainable from one central computer, and settings to keep that hardware operating in a real world environment full of Internet criminals who would install malware to ruin the lab for everyone.
In this series of articles we have installed both Linux and Microsoft Windows 10 Operating Systems (O/S). Each operating system has it’s own configuration needs. In this article we will discuss the configuration settings specific to Linux. Keep in mind that computer security is an oxymoron and security by its own nature must constantly improve. What I suggest in this article is what we have done here, but we may use different approaches in the future. There are many opinions and useful ideas available for configuring Linux on the Internet.
In the next article I intend to share the setup and settings we use for our central server that controls and helps update all the other computers in the lab. Hint: this server, which manages our software updates, some configuration changes, script changes, and even provides weather data to all the workstations is not a $1000 x86 box. It is a $100 (complete) Raspberry Pi 4B and it is awesome.
Why Linux?
One reason that an organization could decide not to use proprietary (Microsoft) software would be if the cost of the software went up. This was the logic expressed by CERN, European Organization for Nuclear Research, the people with the Large Hadron Collider, last summer (https://www.pcmag.com/news/368987/cern-is-ditching-microsoft-due-to-10x-higher-license-fees). Other reasons could include oderous legal records keeping requirements to document and legally prove ownership of all needed licenses, a desire for more control of what is in the programs, concerns about privacy and corporate scraping and sharing of patrons’ private information, or clandestine mal-ware and virus downloads. Also, if an organization provides employment training (as we do) then it must consider which technology the employer(s) prefer. If an organization is extremely well funded it may decide to buy Apple computers to meet these goals, and if not, it would most likely choose to install Linux.
Debian Linux (Ubuntu, Mint / MATE, etc)
Debian is one of the major branches of Linux along with Slackware and Red Hat. MANY different distributions “Distros” are made beginning with Debian and adding or configuring things in different ways. Distro Watch shows choices available to those seeking a free and freely available operating system for their computer. Many Distros are dedicated to special purposes such as video editing, music mixing / performance, security monitoring, home theaters, and other purposes. From Debian.org:
The Debian Project is an association of individuals who have made common cause to create a free operating system. This operating system that we have created is called Debian.
Debian systems currently use the Linux kernel or the FreeBSD kernel. Linux is a piece of software started by Linus Torvalds and supported by thousands of programmers worldwide. FreeBSD is an operating system including a kernel and other software.
However, work is in progress to provide Debian for other kernels, primarily for the Hurd. The Hurd is a collection of servers that run on top of a microkernel (such as Mach) to implement different features. The Hurd is free software produced by the GNU project.
A large part of the basic tools that fill out the operating system come from the GNU project; hence the names: GNU/Linux, GNU/kFreeBSD, and GNU/Hurd. These tools are also free. https://www.debian.org/intro/about#what
Debian Linux is the starting point for several popular Linux distributions, including Ubuntu and Mint. We use Mint Linux with the MATE (mah-tey) desktop in our classes because the look and feel is already familiar to those who have used Microsoft Windows.
Accounts / Passwords
Our personal thinking in the Unix / Linux community is a bit different from that in the Microsoft world, and passwords are one good example.
Microsoft World
In the Microsoft world, most users are desktop users at home or someone else’s employee, and their approach is to avoid typing passwords as much as possible. Because of this thinking computer owners tend to make one account (only), make that account an administrator (able to change the computer configuration, create or delete users account, install or remove programs) and use that account for everything. The user then does not bother to enter a password when s/he wants to perform a sensitive task, such as installing a program or authorizing access to the computer from other computers or web sites.
This seems convenient for the user, but a Trojan web site can then do the same things as the user, without asking for permission or a password, because the user set up his/her account that way. The major vector for malware infestations is drive by downloads – where the user is visiting a web site and the web site silently downloads and installs viruses, spyware, or adware on the user’s computer without their knowledge or consent. You can prevent that by doing the same thing that is traditional in the Unix world – use a normal, non-administrative account for daily use and log in as an administrator (or “shell” to administrator) briefly to install apps or change the inner workings of the computer. But we don’t. Because it seems like too much trouble.
Linux World
Linux users are a special kind of person. Diverse, opinionated, sometimes less tactful than is socially acceptable in polite society, but we want to get our jobs done with minimum work and we don’t like being sidetracked by unnecessary complications such as malware infestations. In some ways we are, well, self-centered jerks. Our computer is OURS, and we expect it to obey US. So our approach to passwords is a bit different and we get a much more secure situation than most people using Microsoft – because of how we think, not because the actual O/S is so much better. Microsoft can be configured to do this, but most will not configure it so.
In the Unix / Linux world we have one account for us, and another for administration. Since we frequently use the command line for quick changes, it is a very small matter to quickly “shell up” to the administrator account, called “root”. You just press CTRL-ALT and then tap T to open a terminal window, type “sudo” or “su -” and the command(s) you want the computer to run, then type “exit” to close the terminal window. Before the computer will comply, it first asks you to tell it the password for “root”. Even if a Trojan web site could do this (most cannot) you would still see this password box jump up in your face while you thought you were just browsing the web, and that makes it really obvious something is going on. We’ll leave retaliation for another lesson.
Our setup
On our lab workstations we first set up the account “manager” as we were installing the O/S, and “manager” can “shell” to “root”. Now we install an account called “usr” for our lab patrons, and it cannot shell to root. We set the password to “let-me-in” just as we did for the Microsoft Windows Walk Up User in the previous article.
Click Menu, then type “user” into the search box. The Users and Groups app will then appear at the top. Press ENTER (or click it) to start the Users and Groups app.
Click Add to add a new user, enter “Walk Up User” in the name and “usr” in the login. Press OK. In the next screen enter the password “let-me-in” (it will echo as * on your screen instead of readable letters) and click OK. The Users and Group app will return to its original screen and you will see the Walk Up User account. Click Change in the Account Type row, and select Desktop User – you don’t want patrons using this general account for the public to change your workstation settings. Click OK and you are done. Account created.
Mega Administrator Hint:
If the user account gets messed up all you need to do to fix it is to start the Users and Groups app again, click on Walk Up User, click delete, and that will delete the account. Be certain to select Delete All Files when you delete. Then click ADD to add a new user, and proceed as above – your Walk Up User account will be fresh and new again, and it cost you about two minutes of your time. Radically different from Microsoft in this regard as desktop users cannot alter the Linux system files.
Additional Software
At this point you already have a very serviceable lab. Your GNU/Linux computers will work individually as do the Microsoft Windows computers: people can sit down and browse the Internet, and you can install software using the Software Manager app in the menu. There is a search box next to the menu like Microsoft, and menus like Microsoft.
To install software with the nice GUI app, open the menu and type “Software” in the search box. Software Manager will appear at the top of the right column. Press Enter or click it.
In the search box at the top of the software manager type what you are looking for and the app will show you a list of possible programs. Click what you want.
If you just want to explore, for example games, leave the search box empty and click one of the big colorful squares in the middle of the Software Manager related to the type of app in which you are interested.
If the following information makes you feel like your brain is trying to flee out one of your ears you can stop – you already have nicely working computers. You can stop for now and come back to do this later if you decide you feel more confident and want to take operation of your lab up a notch so it (mostly) maintains itself and sends you a report in email each night.
We use several helpful programs on the Linux O/S in our workstations. First I’ll give you a list and what each is for, and then I will give you command line instructions to install and configure them. We’re talking copy / paste here for your convenience.
| unattended-upgrades | allows the nightly maintenance script to update programs without needing your personal attention. Otherwise you must manually do the updates. |
| clamtk | anti-virus – scans the workstation and gives a list of all apparent malware via email for you to take appropriate action, such as deleting the malware file(s) |
| openssh-server | Provides communication between your desktop and all your lab computers using secure encrypted shell, hence the name, ssh – Secure SHell |
| fail2ban | blocks future attempts from hackers to break into your workstations. Most hacks are brute-force low tech attempts to guess your password, and will fail each time. When a hack attempt has failed X times from the same IP address, fail2ban blocks their IP address for a period of time. |
| sendemail | Sends a dumb simple email using a login and password that you provide. We use it to easily email us the maintenance logs each night. Seeing the logs the next day gives us a simple and fast way to see all the workstations updated. If we do not see an email from one workstation then we know that we should see what happened. Usually it is because Microsoft got half updated that day, and we just let the Microsoft update app finish its job. |
| apcupsd | We use APC BackUPS and SmartUPS backup power supplies. This app connects their intelligent link to the workstation, so you can see the backup batteries’ charge status and how many minutes you can work should the electrical line power fail. |
| google-chrome-stable | Most popular web browser at this time: Google Chrome |
| conky | Impressive looking computer status monitor. |
Administrator hint:
You know already COPY is Ctrl-C: you highlight the text you want to copy with the mouse and while holding down control you tap C. Paste in a GUI is Ctrl-V. To paste in terminal with the keyboard you must use Ctrl-Shift-V, but you can alternatively right click inside the terminal box and select Paste from the drop down menu.
To do this, CTRL-ALT-T to open terminal (or click terminal in the main menu). Then enter:
manager@ALT-FW-099:~$ su –
Password: (type your root account password here)
root@ALT-FW-099:~# apt install unattended-upgrades clamtk openssh-server fail2ban sendemail apcupsd google-chrome-stable conky
This will install the software. Any of these apps that you do not want, just don’t put them in that line. For example, if you don’t use APC UPSs, then just leave out apcupsd. If you don’t want Google Chrome then leave out google-chrome-stable. You may install them later by typing “apt install” and the package name.
Some configuring is needed to make the programs work well. In the Unix world we feel that the person who owns the computer should be able to do anything they wish with their own computer, so long as they are not harming others. Because of this commitment to Individual Liberty, we heavily document our configuration files with (sometimes) helpful comments, to help anyone who is using our program understand how to bend it to their own will. You can read the comments in these configuration files and adjust the program’s operation to your taste. Or not! It’s up to you!
Configurations
We configure our system using plain text files, readable in normal English. The hardest part is knowing *where* these files are located, not adjusting them. A simple Google Search will usually take you to an abundance of information and opinion on the “best” way of configuring things.
unattended-upgrades
Unattended Upgrades allows your workstations to maintain themselves at night and send you details in email to read the next day. Without enabling unattended upgrades your nightly maintenance script will not actually update much. You want to tell your computer not to ask you for permission for every little thing to be upgraded, you want to tell it to just do it!
You should still be shelled to root, so just type
dpkg-reconfigure unattended-upgrades
nano /etc/apt/apt.conf.d/50unattended-upgrades
You will thus open the nano text editor. You move around with the arrow keys. If you mess up, press CTRL-X to exit (when it asks if you want to save the file type n for No). The commands are across the bottom so you can read them. They are all CTRL-some key.
You should see something like:
// Automatically upgrade packages from these (origin:archive) pairs
//
// Note that in Ubuntu security updates may pull in new dependencies
// from non-security sources (e.g. chromium). By allowing the release
// pocket these get automatically pulled in.
Unattended-Upgrade::Allowed-Origins {
“${distro_id}:${distro_codename}”;
“${distro_id}:${distro_codename}-security”;
// Extended Security Maintenance; doesn’t necessarily exist for
// every release and this system may not have it installed, but if
// available, the policy for updates is such that unattended-upgrades
// should also install from here by default.
“${distro_id}ESM:${distro_codename}”;
//”${distro_id}:${distro_codename}-updates”;
// “${distro_id}:${distro_codename}-proposed”;
// “${distro_id}:${distro_codename}-backports”;
};
Uncomment the line about “${distro_id}:${distro_codename}-updates”; by using the arrows to move down to that line and then using delete or backspace to remove the two slashes at the start of the line.
Unattended-Upgrade::Allowed-Origins {
“${distro_id}:${distro_codename}”;
“${distro_id}:${distro_codename}-security”;
// Extended Security Maintenance; doesn’t necessarily exist for
// every release and this system may not have it installed, but if
// available, the policy for updates is such that unattended-upgrades
// should also install from here by default.
“${distro_id}ESM:${distro_codename}”;
“${distro_id}:${distro_codename}-updates”;
// “${distro_id}:${distro_codename}-proposed”;
// “${distro_id}:${distro_codename}-backports”;
};
Tap CTRL-O to save the file, and CTRL-X to exit the nano editor. If you really mess up, just press CTRL-X to exit without saving first and try again.
Openssh-server
SSH is the Secure SHell app. It allows you to control your workstations from your Unix-like (Linux, Mac, FreeBSD, and others) desktop, even if your desktop is on the other side of the world. SSH also works on Microsoft Windows, if you install the Microsoft flavor of the OpenSSH app. See https://docs.microsoft.com/en-us/windows-server/administration/openssh/openssh_overview.
The communication channel is encrypted and does not need you to install a complicated “virtual network”, does not need you to use a 3rd party such as LogMeIn.com, or any such annoyance. You simply connect to each workstation using its IP address, for example, if the workstation’s IP address is 10.100.1.112:
ssh manager@10.100.1.112
It then asks for the password for manager on the workstation, not your desktop, as you are logging into the workstation. NOTHING WILL APPEAR as you type in the password, just type it and press ENTER. You will then get a command line which is actually running inside the remote workstation and you are ready to go. You can be anywhere, hotel room, your house, or Trump Tower – doesn’t matter. Encrypted, secure and no nonsense connected.
This also works with the graphical file browser on your desktop – you can connect with your file browser and drag / drop / edit stuff as if it was on your desktop. In the Unix world we expect this kind of no nonsense accommodation. To connect using your desktop file browser open the browser and click File, then Connect to Server.
Using Keys instead of Passwords
You can (but are not required to) take this a step further by installing “keys” on your computer. The modern type of key is the “ed25519” key. Older types are the DSA and RSA keys, which have or could be hacked to break your privacy encryption. Another Us Government type exists, the escda key. If you dig deep the whole topic can become mind boggling, but what you actually *need* to do is simple. Just a couple of steps and its done and you can forget about it.
By installing a key you get rid of the need to type a password because the computers will know each other thereafter. If you need to access from a new computer then you will need to use your password, but once keys are set up between your desktop and your workstations you just click and you are connected. Lots of information is available at https://www.ssh.com/ssh/keygen.
To install the keys, open a terminal window (CTRL-ALT-T or click on the terminal). USE YOUR NORMAL ACCOUNT, don’t shell to root for this step. If the IP address of the remote workstation is 10.100.1.112 run the following commands:
ssh-keygen -t ed25519
ssh-copy-id -i ~/.ssh/id_ed25519 manager@10.100.1.112
Then type “ssh manager@10.100.1.112” and it should log you in without asking for a password. It will look something like this:
manager@ALT-FW-099:~$ ssh-keygen -t ed25519
Generating public/private ed25519 key pair.
Enter file in which to save the key (/home/manager/.ssh/id_ed25519):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/manager/.ssh/id_ed25519.
Your public key has been saved in /home/manager/.ssh/id_ed25519.pub.
The key fingerprint is:
SHA256:xLiheUxqn4w4UVkt/YenrfNblh8dC+jJZC039SYV02Q manager@ALT-FW-099
The key’s randomart image is:
+–[ED25519 256]–+
| .o +E|
| o.oo .+|
| o +.o. . ..|
| . * + o = …|
| . = + S X =..o|
| + = . * = o++|
| o . + = +o.|
| . o o ..|
| oo. .|
+—-[SHA256]—–+manager@ALT-FW-099:~$ ssh-copy-id -i .ssh/id_ed25519 manager@10.100.1.112
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: “.ssh/id_ed25519.pub”
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed — if you are prompted now it is to install the new keys
manager@10.100.1.112’s password:Number of key(s) added: 1
Now try logging into the machine, with: “ssh ‘manager@10.100.1.112′”
and check to make sure that only the key(s) you wanted were added.manager@ALT-FW-099:~$ ssh manager@10.100.1.112
Welcome to Linux Mint 18 Sarah (GNU/Linux 4.4.0-21-generic x86_64)* Documentation: https://www.linuxmint.com
0 packages can be updated.
0 updates are security updates.Last login: Fri Dec 20 15:01:52 2019 from 10.100.1.51
manager@ALT-FW-002 ~ $
Disabling password authentication to stop most hacking
The most common hacking method is “brute-force” password guessing: a hacker uses a program to try password after password until eventually it hits on a combination that works. If you turn off password authentication then they can’t get in, even if they guess the password, without the key.
If you feel that you will not need to access the workstation from computers by password, you can increase your level of security by rejecting “password authentication” – that is, for someone to login to your workstations they would already need to have the key installed on their computer. Since you can walk right up to the computer yourself and log into it as administrator, you can easily reverse this process if necessary.
To turn off password authentication, simply change the configuration file for ssh like this. Open a terminal window and shell to root ( CTRL-ALT-T and “su -” ). Then edit the sshd_config file with “nano /etc/ssh/sshd_config”.
manager@ALT-FW-002 ~ $ su –
Password:
ALT-FW-002 ~ # nano /etc/ssh/sshd_configFind the line that says PasswordAuthentication yes and change it to no. Make sure it is not commented out by the line starting with a #. Save the file with CTRL-o (‘Oh’) then exit the editor with CTRL-x. Restart the SSH app with systemctl restart ssh.
ALT-FW-002 ~ # systemctl restart ssh
ALT-FW-002 ~ #
fail2ban
Along with disabling PasswordAuthentication is banning attempts to connect from a hacker. Normally, so long as you use an uncommon password, hackers will need more than three attempts to guess your manager account password and break in. If you use common passwords they might get in the first try. A list can be found on WikiPedia at https://en.wikipedia.org/wiki/List_of_the_most_common_passwords. None of these passwords, or anything close, should ever be used for an administrator capable account (root, manager) in your lab. It doesn’t matter how clever someone thinks “password” is for a password, it’s the first thing a hacker will try, right along with “123456”.
Fail2Ban notices when someone tried to connect via SSH and FAILS. It then bans their IP address for some random period of time. This is sufficient to aggravate most automatic hacking programs and it will look elsewhere for its next victim. Fail2ban will work fine as is, or you can read more on configuring it to your personal preferences at https://www.fail2ban.org/.
APCupsd
The American Power Corp (APC) provides our Uninterruptible Power Supplies UPSs). Since we like using CONKY to show (in our humble opinion) classy and helpful status information, we can also see the status of the battery charge and how long the workstation will continue to run should line power become unavailable. Plus it impresses non-technical people. But to access the APC UPS it is needed to install the apcupsd program and the configuration is simple text files (which is typical in the Unix world) but there are two files to change. More can be read on-line at http://www.apcupsd.org.
 Open a terminal window (CRL-ALT-T), shell to root (su -) and edit the first (of two) configuration files: nano /etc/apcupsd/apcupsd.conf. Find the line that starts with UPSCABLE. Change the UPS Cable type to usb (UPSCABLE usb). Likewise find the line that starts with UPSTYPE and change UPS Type to usb (UPSTYPE usb). Comment out the line that starts with DEVICE by putting a hash character (#) as the first thing on the line. Finally down lower in the file see the line that starts NISIP and set it to NISIP 0.0.0.0.
Open a terminal window (CRL-ALT-T), shell to root (su -) and edit the first (of two) configuration files: nano /etc/apcupsd/apcupsd.conf. Find the line that starts with UPSCABLE. Change the UPS Cable type to usb (UPSCABLE usb). Likewise find the line that starts with UPSTYPE and change UPS Type to usb (UPSTYPE usb). Comment out the line that starts with DEVICE by putting a hash character (#) as the first thing on the line. Finally down lower in the file see the line that starts NISIP and set it to NISIP 0.0.0.0.
When you are done it should look something like this, with plenty of stuff between these lines:
UPSCABLE usb
…
UPSTYPE usb
#DEVICE /dev/ttyS0
…
NISIP 0.0.0.0
Ctrl-O to save and Ctrl-X to exit.
Next edit /etc/default/apcupsd with nano /etc/default/apcupsd. Change the line isconfigured=no to isconfigured=yes.
CTRL-O to save then CTRL-X to exit the editor.
GRUB Bootloader timeout
If you are dual booting then you may wish to change the timeout for the GRUB bootloader to something long enough that people have a chance to choose which system they want to load. We are having good success by setting this to 90 seconds. If you are using only Linux you don’t need to bother with this: if you are using only Microsoft Windows then you would not be reading this article 8).
To change the timeout on the GRUB bootloader, shell to root (su -) and edit the GRUB file with ”nano /etc/default/grub”. Change the line near the top that starts with GRUB_TIMEOUT to read GRUB_TIMEOUT=90.
# If you change this file, run ‘update-grub’ afterwards to update
# /boot/grub/grub.cfg.
# For full documentation of the options in this file, see:
# info -f grub -n ‘Simple configuration’GRUB_DEFAULT=0
GRUB_TIMEOUT_STYLE=hidden
GRUB_TIMEOUT=90
GRUB_DISTRIBUTOR=`lsb_release -i -s 2> /dev/null || echo Debian`
GRUB_CMDLINE_LINUX_DEFAULT=”quiet splash”
GRUB_CMDLINE_LINUX=””
Save the file with CTRL-o and exit the editor with CTRL-x. Now update the bootloader with update-grub. It will look something like this.
root@ALT-FW-099:~# update-grub
Sourcing file `/etc/default/grub’
Sourcing file `/etc/default/grub.d/50_linuxmint.cfg’
Generating grub configuration file …
Found linux image: /boot/vmlinuz-4.15.0-72-generic
Found initrd image: /boot/initrd.img-4.15.0-72-generic
Found memtest86+ image: /boot/memtest86+.elf
Found memtest86+ image: /boot/memtest86+.bin
Found Windows 10 on /dev/sda1
done
root@ALT-FW-099:~#
When you next boot up the computer it will present the GRUB bootloader screen 90 seconds. Use the keyboard arrows to move up and down until you are on the O/S that you wish to start, then press ENTER, or left arrow, or right arrow to load that O/S.
Conky
Conky is a lightweight free system monitor available on Linux and BSD. It can display the system information and statistics such as CPU consumption, disk usage, RAM utilization, network speed etc in an elegant way. All the information is displayed on top of your wallpaper. It gives your desktop a live wallpaper feel. https://itsfoss.com/conky-gui-ubuntu-1304/.
All that is needed to start conky is a conky configuration file, which is named .conkyrc. Notice that this file name begins with a period. The period tells Linux not to bother you with seeing this file unless you deliberately ask for it – it makes this a “hidden” file. In the file browser merely press CTRL-H to see all the hidden files along with stuff you might want to normally use. My .conkyrc file can be downloaded from here as a starting point (remember to rename it to .conkyrc first), but you will want to change it to fit your own hardware and your personal likes and dislikes. Browse through https://itsfoss.com/conky-gui-ubuntu-1304/ to get the idea of how to use Conky and the github repository is located at https://github.com/brndnmtthws/conky.
To test your own .conkyrc, I suggest that you run it in terminal. Just open a terminal window (CTRL-ALT-T) and type conky. Yes, that’s it. You should see your Conky start up, or if there is something wrong you’ll see lots of text messages in your terminal window. Savor the pain. You can kill execution in terminal with CTRL-C. Welcome to programming. Once you have Conky running as you wish, you might want it to start each time that you log in, instead of your needing to manually start it.
Starting Conky at login
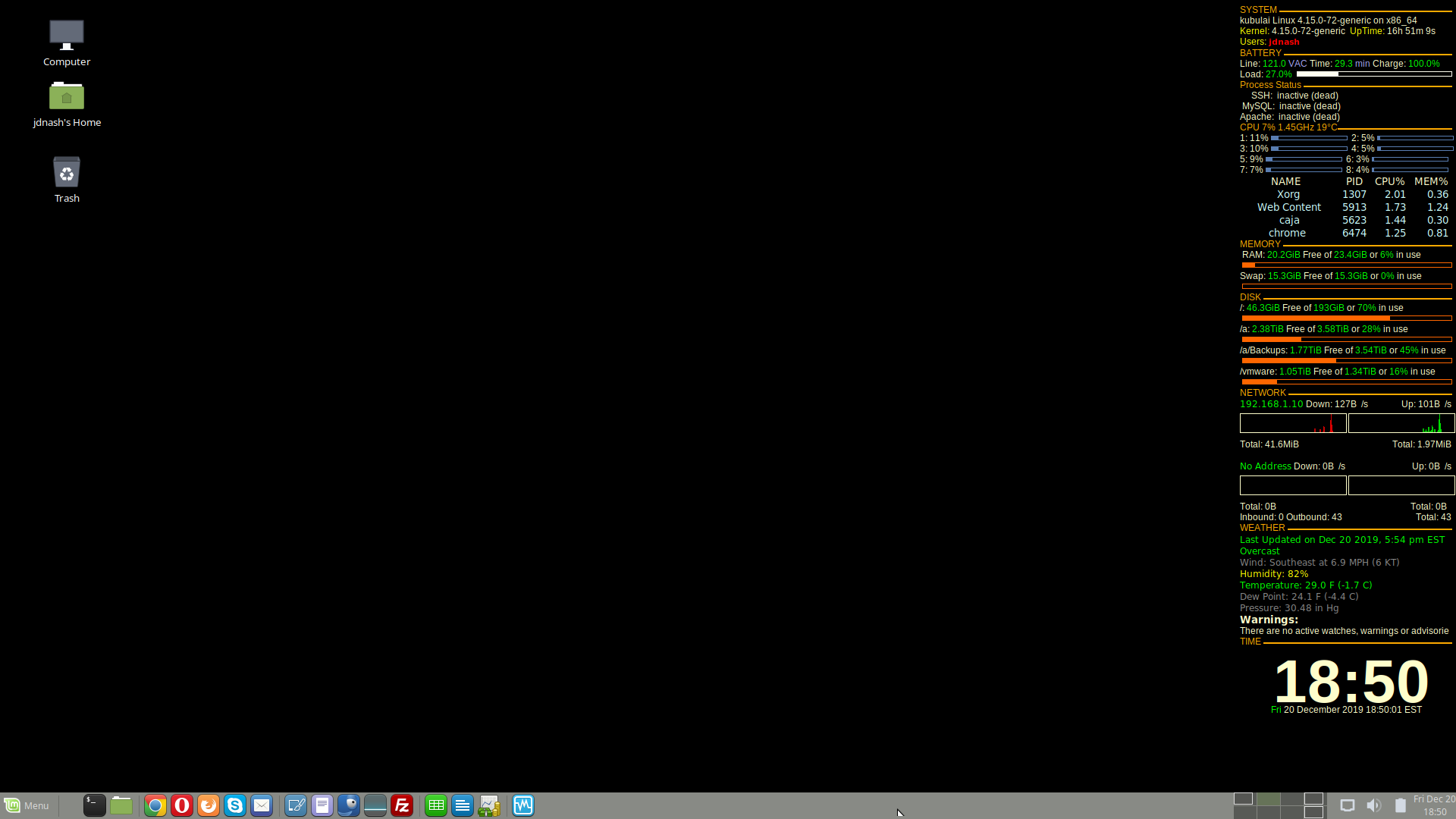
You can start conky from a terminal window, but I like it better when it starts automatically after I log in. In your menu search box type “Startup” and you should see Startup Applications.

Click ADD. In the command: box type conky -d -p 10. The word conky is the command (all lowercase) the option -d means start it in the background, and the option -p 10 means wait 10 seconds before you start it. I added the -p 10 because sometimes conky could not start immediately as the desktop was not yet completely ready, and by adding a little delay the desktop gets enough time to finish starting up before conky tries to start.
Scheduled Program Executions
The last piece of configuring our menagerie of computers is the automatic scheduling using crontab. If you struggle using the command line, it is OK to stop now. Your lab computers will still work, you must merely remember to update them one by one every few days.
Scheduling in GNU/Linux uses a program named cron that lets you automatically start programs whenever you wish – once every two minutes, once a week, once a month, or whatever. Similar to the Microsoft “schedule” functionality but at once it can be both much simpler and more complex.
Cron is driven by a crontab (cron table) file, a configuration file that specifies shell commands to run periodically on a given schedule. The crontab files are stored where the lists of jobs and other instructions to the cron daemon are kept. Users can have their own individual crontab files and often there is a system-wide crontab file (usually in
/etcor a subdirectory of/etc) that only system administrators can edit. https://en.wikipedia.org/wiki/Cron
There is much information available on how to program crontab, but the Wiki article cuts to the heart of the matter: https://en.wikipedia.org/wiki/Cron.
Each computer account can have its own cron table. To configure the crontab log in as that user – for root shell to root like “su -” then type “crontab -e” to configure. The very first time you do this crontab will ask what editor you like to use – I HIGHLY suggest you select NANO as the other choice, VI, is a great editor but complex and very much an acquired taste!
The account usr does not need a crontab, so we start with the manager account. Login as manager and open a terminal window.
At the command line type “crontab -e”. At the bottom add the line “*/2 * * * * ~/weather-fetch.sh”. It should look like this:
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use ‘*’ in these fields (for ‘any’).#
# Notice that tasks will be started based on the cron’s system
# daemon’s notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
*/2 * * * * ~/weather-fetch.sh
Then Ctrl-O, Ctrl-X and crontab is updated and you are back at the command line. This will run the script named weather-fetch.sh in manager’s home folder, /home/manager/weather-fetch.sh. Because this crontab is running in the manager account, the tilde (~) means manager’s home folder, or /home/manager. It is a shortcut: when we type ~ it means the home folder for the account.
Now this will run the file “weather-fetch.sh” every two (2) minutes. This file is referrred to as “a script” file. It contains computer commands in the BASH (BAsic SHell) language, which is very similar to the old Microsoft DOS batch language. A sample is below:
#!/bin/bash
#weather-process.sh
#author: John D. Nash, Jr. API LLC
#last_update: 20191219 JDN
#comments: fetches various stuff from the lab server to the lab workstations
# expects wwraw.xml and walerts.xml downloaded from NOAA by cron job once per hour by the lab server
# lab computers fetch the needed weather information from the local server and distributes it as needed on the local workstation
# instead of directly from NOAA to be respectful of the NOAA utilization load
#
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
DEBIAN_FRONTEND=noninteractive#current weather status
rsync –rsh=ssh –checksum –quiet manager@ALT-FW-RPi:wwraw.xml wwraw.xml
rsync –rsh=ssh –checksum –quiet wwraw.xml /home/usr/wwraw.xml#weather alerts
rsync –rsh=ssh –checksum –quiet manager@ALT-FW-RPi:walerts.xml walerts.xml
rsync –rsh=ssh –checksum –quiet walerts.xml /home/usr/walerts.xml#Mark Execution Time
touch weather-fetch-time.txt#conkyrc
rsync –rsh=ssh –checksum –quiet manager@ALT-FW-RPi:\.conkyrc \.conkyrc
rsync –rsh=ssh –checksum –quiet \.conkyrc /home/usr/\.conkyrc#nightly.sh
rsync –rsh=ssh –checksum –quiet manager@ALT-FW-RPi:nightly.sh nightly.sh
You may copy / paste this into a file and name it weather-fetch.sh, then make the file executable by also typing the command “chmod +x weather-fetch.sh”.
We can gently look at what this script does without digging too deeply in how it works. The first file transferred is wwraw.xml. The program called rsync is used to collect it from the lab’s server, which is named ALT-FW-RPi. ALT-FW-RPi could just as well be the IP address of the server, such as 10.100.1.123: if 10.100.1.123 is the IP address of ALT-FW-RPi then “rsync –rsh=ssh –checksum –quiet manager@10.100.1.123:wwraw.xml wwraw.xml” is the same thing as “rsync –rsh=ssh –checksum –quiet manager@ALT-FW-RPi:wwraw.xml wwraw.xml”.
rsync –rsh=ssh –checksum –quiet manager@ALT-FW-RPi:wwraw.xml wwraw.xml
Rsync is already part of GNU/Linux. Rsync is used here because it is smart enough to know if the file is any different from the file already on the workstation, and if the files are the same it does NOT bother downloading it! This command instructs rsync to use the file’s checksum (it could also use it’s file date or file size) to decide if the file on the server is already the same thing as exists on the workstation. A copy command (in GNU/Linux cp or scp) would just download it again anyway.
There is an abundance of information on rsync available at https://en.wikipedia.org/wiki/Rsync and other web sites.
The “–rsh=ssh” means that rsync should use the ssh file transfer program that we have already installed, and since we installed ed25519 keys both computers already know each other and no passwords need to be manually typed – it just works! The next line copies the wwraw.xml file to the usr account if the same thing is not already there: the usr account also runs conky to display weather and other statistics, so a copy of the weather information gets updated in the usr account too. The next two lines do the same thing for the weather alerts file, walerts.xml, then the next two lines do the same thing for the .conkyrc file.
The last lines update the nightly batch script but they leave it in the manager’s home folder and do not copy it elsewhere. At night this nightly.sh file will execute to maintain the workstation: scan for viruses, remove unauthorized software installed during the day, update software with new versions, and so forth. This allows all the workstations to be updated by simply changing the files on the server, and the updated files are automatically copied to every workstation within two (2) minutes.
Next shell to root in the terminal window by typing the command “su -” and change the root crontab (crontab -e, choose nano, add the line at the bottom, Ctrl-O, Ctrl-X) so it looks like this:
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use ‘*’ in these fields (for ‘any’).#
# Notice that tasks will be started based on the cron’s system
# daemon’s notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
15 1 * * * /root/nightly-cron-job.sh >/dev/nul 2>&1
00-59 17 * * 1,2,3,4,5 /sbin/halt -p
30-59 16 * * 1,2,3,4,5 cat /root/labclosing.txt | wall
The first line runs the nightly cron job 15 minutes after the hour of 1:00AM every night. This is in a script named “nightly-cron-job.sh”. You should still be in the /root folder, which is where you start when you shell to root with “su -“. You can copy / paste this into a file and name it nightly-cron-job.sh. Remember to make the file executable by also typing the command “chmod +x nightly-cron-job.sh”.
#!/bin/bash
NOW=$(date +”%Y%m%d-%H%M%S”)
if [ -x “/home/manager/nightly.sh” ];then
echo running nightly batch job instructions $NOW
. /home/manager/nightly.sh
else
echo No nightly batch instructions to run $NOW
fiNOW=$(date +”%Y%m%d-%H%M%S”)
echo ===
echo $HOSTNAME batch job done $NOW
echo ===
The next line in the cron table shuts off the workstation at 5:00pm sharp (give or take a minute or so) and if the computer is restarted it will shut it down again and again as soon as it gets booted up, until 6:00pm. This encourages patrons to leave the lab when we are closed without our staff having to experience negative interactions with patrons who do not want to leave. We learned to do this by bad experiences with patrons, not a desire to make things complicated.
The last line in the cron table displays a warning message to all users before the computer shuts down. It’ll keep showing this warning from 4:30pm every two (2) minutes or so until the computer turns itself off at 5:00pm. It is intended to be annoying – we close at 4:00pm. To create this message, (you should still be in the /root folder, which is where you start when you shell to root with “su -“) type “nano labclosing.txt” and paste in the following, or type whatever other text you prefer instead: it is merely text to be displayed:
***************************************************************************
** The Bridge Room Lab is now closing. Please save your work and log off **
***************************************************************************The Bridge Room is normally open weekdays from 9:00AM until 4:00PM,
at which time the computers are programmed to shut down automatically.
Please save your work at this time and log off. Or not. Your call.
How lucky do you feel?
I will go into detail on the nightly.sh scrip file in the next article. I will also discuss our Raspberry Pi server configuration and how to download the current weather from NOAA once an hour onto the server, so that you do not have 20 workstations all hammering NOAA with downloads every two (2) minutes, which could get your direct access to NOAA weather data blocked.










You must be logged in to post a comment.